![]() (1)
(1)
![]() (2)
(2)
Where UNIF(.) - unification procedure;
![]() (.) - virtualization procedure defining j-measurement;
(.) - virtualization procedure defining j-measurement;
![]() - initial key formed on the basis of given key data
- initial key formed on the basis of given key data ![]() ;
;
![]() - projection of virtual key onto j-measurement;
- projection of virtual key onto j-measurement;
The unfolded key is formed by obtained virtual key devirtualization:
![]() (3)
(3)
Expressions (1) - (3) define common algorithm of unfolded key creation at multivariate performance of key bands virtual sample spaces. The concrete definition of the given algorithm is carried out by unification procedure definition . Variants of such concrete definition are represented by expressions (4) and (5)
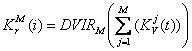 (4)
(4)
 (5)
(5)
Software implementation of the algorithms given in expressions (4), (5) allowed software encryption complex creation, which opens a possibility of absolute undeciphering capability support. Experimental researches of the complex confirm its significant potential possibilities. Given results are obtained during researches at Russian Federation Education Ministry grant T02-03.1-816 support.
The bibliographic list
- Kotenko V.V., Polycarpov S.V. The strategy of key bands virtual sample spaces creation at information protection problem solving//Information Security Problems . 2002. №2. p 47-52.



